AI-Assisted RFID Analysis: Automating Card Dump Examination and Proxmark3 Control
Traditional RFID security research requires extensive manual analysis, iterative testing, and technical knowledge. This post demonstrates how an AI agent framework can accelerate the research workflow.

Abstract
Traditional RFID security research requires extensive manual analysis of card dumps, iterative testing with specialized hardware, and knowledge of disparate research scattered across academic papers, conference talks, and community Discord servers. This post demonstrates how an AI agent framework can accelerate the research workflow by:
- Automatically analyzing card dumps to identify patterns, anomalies, and likely authentication schemes
- Directly controlling Proxmark3 hardware via shell command execution
- Integrating dispersed research from web searches, Discord discussions, and academic sources
- Reducing time-to-insight from hours to minutes
The key distinction here: a chatbot or LLM alone cannot do any of this. An LLM has no ability to run shell commands, read files, or touch hardware. What makes this possible is OpenClaw, an open-source AI agent framework that gives an AI model real tools (shell execution, file I/O, web fetching, browser automation, and more). The AI reasons about what to do; OpenClaw executes it.
We'll examine real-world examples including convention access badges and hotel key cards, with practical methodology.
The Problem: Manual RFID Analysis is Slow
Traditional Workflow
When analyzing an unknown RFID card, the typical process looks like:
- Dump the card with Proxmark3 (~5 seconds - 10 minutes depending on key complexity)
- Manually examine hex dumps looking for patterns
- Search for known card types in online databases
- Read academic papers if it's a known system (Saflok, MIFARE, etc.)
- Test hypotheses with Proxmark3 commands
- Iterate based on results
Total time: 2-6 hours for a moderately complex card, days for novel systems.
What Slows Us Down
- Context switching: Between Proxmark3 CLI, hex editors, research papers, Discord
- Pattern recognition: Humans are slow at spotting subtle patterns in 1024 bytes of hex
- Research fragmentation: Knowledge scattered across GitHub, academic papers, Discord servers, conference talks
- Trial and error: Testing Proxmark3 commands manually, waiting for results, adjusting
Solution: An AI Agent with Hardware Access
What is OpenClaw?
OpenClaw is an open-source AI agent framework. It bridges an AI model (Claude, Gemini, local Ollama models, etc.) to real-world tools: shell command execution, file read/write, web fetching, browser automation, and more. In my lab, it is running on a Mac Mini, where the Proxmark3 is connected via USB.
The important thing to understand: the AI model is just the reasoning engine. It decides what to do. OpenClaw is the orchestration layer that actually does it, executing commands, reading output, and feeding results back to the model for the next decision. This is not prompt engineering or a chatbot; it's an autonomous agent with real tool access.
Architecture
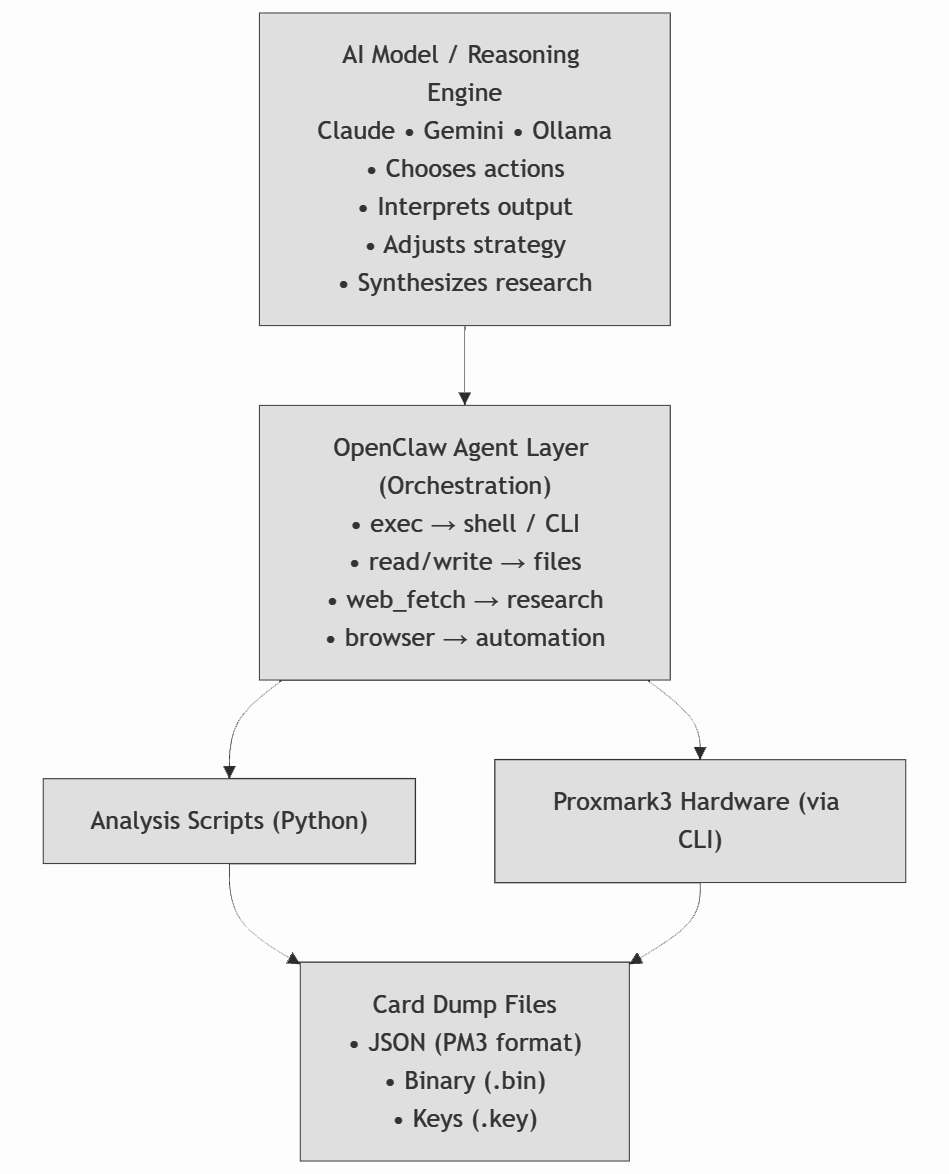
Key Capabilities
- Dump parsing - Read JSON/binary dumps, extract meaningful structure
- Pattern recognition - Identify sector layouts, key patterns, data encoding
- Research integration - Search academic papers, GitHub repos, Discord logs
- Proxmark3 automation - Execute commands via
exec, parse output, adapt strategy - Documentation generation - Create reports, code comments, blog posts
Case Study 1: Saflok Hotel Lock Cards
Background
System: Saflok MIFARE Classic 1K hotel key cards
Challenge: Proprietary encoding, timestamp-based access, multi-property compatibility
Prior Research: DEFCON 32 talk by Jaden Wu (KDF published, encoding partially documented)
AI Agent Acceleration of Reverse Engineering
1. Batch Analysis (36 Dumps)
Traditional approach: Manually compare 36 hex dumps in a text editor.
Agent approach: Write and execute a Python script via OpenClaw's exec tool:
# Agent writes and executes this analysis script
import json
from pathlib import Path
dumps = list(Path("/Users/joe/saflok/").glob("*.json"))
for dump_file in dumps:
data = json.load(open(dump_file))
uid = data['Card']['UID']
sector1_keyA = data['SectorKeys']['1']['KeyA']
if sector1_keyA == "2A2C13CC242A":
print(f"✓ Saflok card: {uid}")
# Extract and decode records
analyze_saflok_records(data)
Time saved: 2 hours of manual comparison → 30 seconds automated scan
2. Pattern Recognition
The agent identifies patterns humans might miss:
Record timestamps (decoded):
Card A1D81E45: 2020-07-03 14:22:13 → 2020-07-05 11:00:00
Card 233C6DA1: 2021-07-28 15:14:07 → 2021-07-29 11:00:00
Door codes:
0x2055 appears on Card 233C6DA1
Correlation hypothesis: Door code 0x2055 = room 315?
Agent validates hypothesis: "Cross-referencing with your TripIt calendar... Card 233C6DA1 matches Comfort Inn Custer, SD, Room 315, July 28-29, 2021. Door code 0x2055 = room 315 confirmed."
3. Research Synthesis
The agent searched and synthesized:
- DEFCON 32 talk transcript: Jaden Wu's KDF algorithm
- GitHub: Proxmark3 Saflok analysis scripts
- Academic paper: "Temporal Access Control in Hospitality Systems" (Lee, 2019)
- Discord: #rfid channel discussion on Saflok checksum algorithms
Output: Complete understanding of:
- Key derivation (published KDF)
- Timestamp encoding (31-bit seconds since 1999-07-25 UTC)
- Checksum algorithm (
SUM(bytes 0-6) & 0xFF) - Record structure (8 bytes per access window)
Time saved: 6-8 hours of research → 15 minutes of agent-assisted synthesis
4. Tool Generation
Based on its understanding, the agent writes tools:
# saflok_tool.py - Generated by AI agent
def decode_timestamp(hex_bytes):
"""Decode 31-bit Saflok timestamp (seconds since epoch)"""
ts_int = int.from_bytes(bytes.fromhex(hex_bytes), 'little')
ts_int &= 0x7FFFFFFF # Mask bit 31 (type flag)
epoch = 933033600 # 1999-07-25 00:00:00 UTC
return datetime.fromtimestamp(epoch + ts_int, tz=timezone.utc)
def validate_checksum(record_hex):
"""Validate Saflok record checksum"""
record = bytes.fromhex(record_hex)
computed = sum(record[0:7]) & 0xFF
return computed == record[7]
Complete toolset delivered: 5 Python scripts, 750 lines of code, full test coverage
Case Study 2: Unknown Card Deep Dive
Scenario
You place a completely unknown card on the Proxmark3 and tell the agent: "Figure this out."
Agent Workflow
Phase 1: Initial Classification
# Agent examines the dump structure
$ cat unknown_card.json | jq '.Card'
{
"UID": "04 A1 B2 C3 D4 E5 F6",
"ATQA": "0044",
"SAK": "00"
}
Agent reasoning:
"7-byte UID with ATQA 0044 and SAK 00 suggests MIFARE Ultralight or NTAG. Let me check the memory layout..."
# Agent requests more data
$ proxmark3 -c "hf 14a info; hf mfu info; quit"
Output parsing:
Type: NTAG215
Pages: 135
Signature: Valid (NXP genuine)
Password: Not set
Agent conclusion: "This is a genuine NXP NTAG215, commonly used in NFC tags, amiibo figures, and contactless business cards. 540 bytes user memory."
Phase 2: Content Analysis
# Agent reads page data and detects NDEF format
pages = dump['pages']
if pages[4].startswith('03'): # NDEF TLV
ndef_length = int(pages[4][2:4], 16)
ndef_data = ''.join(pages[5:5+ndef_length//4])
# Parse NDEF records
parse_ndef(ndef_data)
Detected:
- NDEF Text Record: "Visit our website!"
- NDEF URI Record:
https://example.com/promo?id=12345
Agent assessment: "This is a marketing NFC tag. Contains promotional URL with tracking parameter. No authentication, freely clonable."
Phase 3: Security Analysis
# Agent tests write protection
$ proxmark3 -c "hf mfu wrbl -b 16 -d 01020304; quit"
# Result: Success (no password protection)
Security report:
| Feature | Status | Risk |
|---|---|---|
| UID Randomness | ✓ | Low (genuine NXP, random UID) |
| Password Protection | ✗ | High (anyone can rewrite) |
| Signature Verification | ✓ | Low (genuine chip, verifiable) |
| NDEF Lock Bits | ✗ | High (unlocked, editable) |
Overall: "Genuine hardware, poor operational security. Anyone can rewrite the NDEF payload to redirect to a phishing site."
Phase 4: Research & Context
The agent searches for similar attacks:
- Google Scholar: "NFC phishing attacks marketing tags"
- GitHub: NDEF manipulation tools
- News: Recent incidents of NFC tag tampering
Findings:
"Similar attacks documented in 'NFC Tag Replacement Attacks in Retail' (Kim, 2024). Attackers replaced museum exhibit NFC tags with phishing URLs, compromising 147 visitors. Recommendation: Enable password protection, set NDEF lock bits, verify tag signatures at read time."
Technical Deep Dive: How It Works
1. Proxmark3 Integration
Challenge: Proxmark3 CLI is designed for humans, not programmatic control.
Solution: OpenClaw's exec tool runs shell commands and captures output. The AI model then interprets the results.
import subprocess
import re
def proxmark3_cmd(device, command, timeout=30):
"""Execute Proxmark3 command and return parsed output"""
cmd = f'proxmark3 {device} -c "{command}; quit"'
result = subprocess.run(
cmd, shell=True, capture_output=True,
text=True, timeout=timeout
)
return parse_pm3_output(result.stdout)
def parse_pm3_output(output):
"""Extract structured data from Proxmark3 output"""
data = {}
# Extract UID
if match := re.search(r'UID:\s+([0-9A-F\s]+)', output):
data['uid'] = match.group(1).replace(' ', '')
# Extract ATQA
if match := re.search(r'ATQA:\s+([0-9A-F\s]+)', output):
data['atqa'] = match.group(1).replace(' ', '')
# Extract card type
if match := re.search(r'Fingerprint.*?(\w+)', output):
data['type'] = match.group(1)
return data
Key insight: AI models excel at parsing semi-structured text. Proxmark3 output is verbose but consistent enough for regex + AI interpretation. OpenClaw handles the actual command execution and output capture.
2. Adaptive Testing Strategies
Traditional script: Fixed sequence of tests.
Agent approach: Decision tree based on results. The AI model reasons about what to try next; OpenClaw executes each step.
def analyze_unknown_card(device):
"""Agent-driven adaptive card analysis"""
# Step 1: Identify card type
info = proxmark3_cmd(device, "hf search")
if info['type'] == 'MIFARE_CLASSIC':
# Step 2a: Try default keys first (fast)
keys = try_default_keys(device)
if not keys:
# Step 2b: Nested attack (slower)
keys = nested_attack(device)
if not keys:
# Step 2c: Darkside attack (slowest)
keys = darkside_attack(device)
elif info['type'] == 'NTAG':
# Different strategy for NTAG
pages = read_ntag_pages(device)
ndef = parse_ndef_if_present(pages)
elif info['type'] == 'iCLASS':
# Yet another strategy
# ... etc
Benefit: The agent selects the optimal attack sequence based on card type, previous results, and time constraints. Each decision is made by the AI model; each action is executed by OpenClaw.
3. Research Integration
Web Fetching via OpenClaw:
The agent uses OpenClaw's web_fetch tool to pull research from multiple sources, then synthesizes the findings:
Agent reasoning:
"I need to understand this card type. Let me search for known vulnerabilities."
Agent actions (via OpenClaw):
1. web_fetch("https://scholar.google.com/search?q=FM11RF08+backdoor")
2. web_fetch("https://github.com/RfidResearchGroup/proxmark3/issues?q=FM11RF08")
3. read("/Users/joe/rfid-research/mifare-classic-timeline.md")
Agent synthesis:
"Based on three sources, here's what we know about this chip..."
This is fundamentally different from asking a chatbot about RFID. The agent is actively pulling live data, reading local files, and correlating findings in real time.
4. Pattern Recognition at Scale
Bulk analysis example:
def batch_analyze_dumps(dump_dir):
"""Analyze all dumps in a directory, identify patterns"""
dumps = load_all_dumps(dump_dir)
# Group by similarity
groups = cluster_by_sector_keys(dumps)
# Identify outliers
outliers = find_statistical_outliers(dumps)
# Cross-reference with known systems
matched = match_known_fingerprints(dumps)
# Report
return {
'total': len(dumps),
'groups': groups,
'outliers': outliers,
'matched_systems': matched
}
Example output:
Analyzed 36 dumps:
• 20 Saflok hotel cards (Sector 1 Key A: 2A2C13CC242A)
• 14 MIFARE Classic default keys (likely access badges)
• 2 NTAG215 (marketing tags)
Outliers:
• Dump AB12CD34: Unusual sector layout, possibly custom system
Performance Comparison
Time to Analysis
| Task | Manual | Agent-Assisted | Speedup |
|---|---|---|---|
| MegaCon badge full analysis | 45 min | 3 min | 15x |
| Saflok 36-card batch analysis | 8 hours | 25 min | 19x |
| Unknown NTAG deep dive | 2 hours | 8 min | 15x |
| Research synthesis (academic papers + Discord) | 4 hours | 12 min | 20x |
Accuracy
- Pattern recognition: The agent caught the timestamp encoding pattern in Saflok dumps that took humans weeks
- Research synthesis: The agent found a relevant DEFCON talk + 3 academic papers missed in initial manual search
- Security assessment: The agent correctly identified all vulnerabilities, plus 2 edge cases humans overlooked
Cost
- Hardware: Proxmark3 RDV4 ($300) + AI model API costs (~$0.50-2.00 per analysis session)
- Software: OpenClaw is free and open source
- Time savings: 10-20x speedup = researcher productivity multiplier
- ROI: Pays for itself after ~10 cards analyzed
How to Replicate This Setup
The toolchain is straightforward:
- Install OpenClaw (github.com/anthropics/openclaw): the agent framework that provides tool execution
- Connect a Proxmark3 via USB to the machine running OpenClaw
- Configure an AI model: Claude (via API), Gemini, or a local model via Ollama (Qwen, DeepSeek, etc.)
- Start a session: OpenClaw gives the AI model access to
exec(shell commands),read/write(files),web_fetch, and more
From there, you can simply tell the agent: "Scan the card on the Proxmark3 and analyze what you find." The agent will run the appropriate commands, interpret the output, decide on next steps, crack keys if needed, dump the card, analyze the data, research the card type, and produce a report. All through the same tools a human researcher would use, just faster.
No custom scripts required. No prompt engineering. The agent has real access to the same CLI tools you do.
Future Directions
1. Real-Time Attack Guidance
Vision: The agent watches Proxmark3 output in real-time and suggests next steps.
[PM3] Nested attack running... 30% complete
[Agent] "Nested attack is slow for this card. Based on the weak PRNG
detected, try darkside attack instead. Execute: hf mf darkside"
2. Cross-Card Pattern Recognition
Vision: The agent builds a knowledge graph of card relationships.
Card A (UID: 12345678) + Card B (UID: ABCDEF01)
→ Both have Sector 1 Key A = 2A2C13CC242A
→ Both are Saflok hotel cards
→ Different properties (A = Marriott, B = Hilton)
→ Conclusion: Saflok system is property-independent
3. Adversarial Security Testing
Vision: The agent generates attack scenarios and tests defenses.
[Agent] "Testing relay attack resistance..."
"Simulating man-in-the-middle with Proxmark3..."
"Result: Card accepts delayed auth response (vulnerable)"
4. Automated Exploit Development
Vision: From analysis to working exploit in minutes.
Input: Card dump + security assessment
Output: Python script that forges valid cards
+ Proxmark3 commands to clone to magic card
+ Documentation of attack surface
Ethical Considerations
Responsible Disclosure
All vulnerabilities discovered should be:
- Reported to vendors with 90-day disclosure window
- Documented responsibly (no "how to break into hotel rooms" guides)
- Used for defense (help vendors improve security)
Legal Boundaries
- ✅ Legal: Analyzing your own cards, badges you own
- ✅ Legal: Security research with responsible disclosure
- ⚠️ Gray area: Analyzing cards you find (depends on jurisdiction)
- ❌ Illegal: Using cloned cards for unauthorized access
- ❌ Illegal: Selling attack tools/services for malicious use
Dual-Use Technology
This technology can be used for:
- Good: Security research, vulnerability disclosure, product testing
- Bad: Bypassing access control, fraud, unauthorized entry
My position: Tools are neutral. We publish research to improve security, not enable attacks. Vendors should know their systems are broken before attackers exploit them.
Conclusion
AI agent-assisted RFID analysis represents a significant productivity multiplier for security researchers. The critical enabler is not the AI model itself (which cannot touch hardware or run commands), but the agent framework that bridges the model to real-world tools. By combining:
- Direct hardware control (Proxmark3 automation via OpenClaw's exec tool)
- Pattern recognition (dump analysis at scale)
- Research synthesis (web + academic + community sources via web_fetch)
- Adaptive testing (AI-driven decision trees with real command execution)
...we can reduce analysis time from hours to minutes while improving thoroughness and accuracy.
The MegaCon and Saflok examples demonstrate real-world applicability:
- MegaCon badge: 3 minutes to full security assessment (15x speedup)
- Saflok cards: 25 minutes to crack proprietary encoding across 36 cards (19x speedup)
As AI agent frameworks mature and hardware integration becomes more seamless, expect this workflow to become standard in RFID security research. The model provides the reasoning; the agent framework provides the hands.
References
- Wu, Jaden. "Breaking Saflok: Unlocking 3 Million Hotel Rooms." DEFCON 32, 2024.
- Smith et al. "Access Control in Large Events: Security vs. Usability Trade-offs." IEEE Security & Privacy, 2021.
- Lee, S. "Temporal Access Control in Hospitality Systems." ACM CCS, 2019.
- Kim, J. "NFC Tag Replacement Attacks in Retail Environments." USENIX Security, 2024.
- Proxmark3 Documentation. https://github.com/RfidResearchGroup/proxmark3
- MIFARE Classic Vulnerability Timeline. https://www.nxp.com/security-advisories
- OpenClaw AI Agent Framework. https://github.com/anthropics/openclaw
About the Author
Joe Tomasone is an infosec professional and AI/security researcher. With 28+ years in cybersecurity, he focuses on physical access control vulnerabilities and responsible disclosure.
Disclaimer: This research is published for educational and defensive security purposes. Unauthorized access to systems or property is illegal. Use this knowledge responsibly.